Siguiente: Redirección Subir: Rack, un Webserver Ruby Anterior: Práctica: Accediendo a Twitter Índice General Índice de Materias
Rack::Auth::Basic implements HTTP Basic Authentication, as per RFC 2617.
WWW-Authenticate: Basic realm="insert realm"
username:password
Basic is then put
before the encoded string.
Aladdin as the username and
open sesame as the password then the header is formed as
follows:.
Authorization: Basic QWxhZGRpbjpvcGVuIHNlc2FtZQ==
Initialize with the Rack application that you want protecting, and a block that checks if a username and password pair are valid.
Puede encontrar el fuente en GitHub
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ cat protectedlobster.rb
require 'rack'
require './lobster'
require 'yaml'
lobster = Rack::Lobster.new
passwd = YAML.load(File.open('etc/passwd.yml').read)
protected_lobster = Rack::Auth::Basic.new(lobster) do |username, password|
passwd[username] == password
end
protected_lobster.realm = 'Lobster 2.0'
pretty_protected_lobster = Rack::ShowStatus.new(Rack::ShowExceptions.new(protected_lobster))
Rack::Server.start :app => pretty_protected_lobster, :Port => 9292
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ cat lobster.rb
require 'rack/request'
require 'rack/response'
module Rack
class Lobster
LobsterString = "a lobster"
def call(env)
req = Request.new(env)
req.env.keys.sort.each { |x| puts "#{x} => #{req.env[x]}" }
if req.GET["flip"] == "left"
lobster = LobsterString.reverse
href = "?flip=right"
elsif req.GET["flip"] == "crash"
raise "Lobster crashed"
else
lobster = LobsterString
href = "?flip=left"
end
res = Response.new
res.write <<-"EOS"
<title>Lobstericious!</title>
<pre>
#{lobster}
</pre>
<p><a href='#{href}'>flip!</a></p>
<p><a href='?flip=crash'>crash!</a></p>
EOS
res.finish
end
end
end
if $0 == __FILE__
require 'rack'
require 'rack/showexceptions'
Rack::Server.start(
:app => Rack::ShowExceptions.new(
Rack::Lint.new(
Rack::Lobster.new)),
:Port => 9292,
:server => 'thin'
)
end
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ cat etc/passwd.yml --- # Indented Block casiano: tutu ana: titi
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ cat Rakefile
...
desc "run the server for protectedlobster"
task :protected do
sh "ruby protectedlobster.rb"
end
desc "run the client with user and password flip left"
task :protectedleft do
sh %q{curl -v --basic -u casiano:tutu 'http://localhost:9292?flip=left'}
end
...
task :crash do
sh %q{curl -v 'http://localhost:9292/?flip=crash'}
end
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ rake protected ruby protectedlobster.rb >> Thin web server (v1.5.1 codename Straight Razor) >> Maximum connections set to 1024 >> Listening on 0.0.0.0:9292, CTRL+C to stop
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ rake protectedleft
curl -v --basic -u casiano:tutu 'http://localhost:9292?flip=left'
* About to connect() to localhost port 9292 (#0)
* Trying ::1... Connection refused
* Trying 127.0.0.1... connected
* Connected to localhost (127.0.0.1) port 9292 (#0)
* Server auth using Basic with user 'casiano'
> GET /?flip=left HTTP/1.1
> Authorization: Basic Y2FzaWFubzpzZWNyZXRv
> User-Agent: curl/7.21.4 (universal-apple-darwin11.0) libcurl/7.21.4 OpenSSL/0.9.8y zlib/1.2.5
> Host: localhost:9292
> Accept: */*
>
< HTTP/1.1 200 OK
< Content-Length: 168
< Connection: keep-alive
< Server: thin 1.5.1 codename Straight Razor
<
<title>Lobstericious!</title>
<pre>
retsbol a
</pre>
<p><a href='?flip=right'>flip!</a></p>
<p><a href='?flip=crash'>crash!</a></p>
* Connection #0 to host localhost left intact
* Closing connection #0
[~/local/src/ruby/sinatra/rack/rack-lobster(master)]$ rake protected ruby protectedlobster.rb >> Thin web server (v1.5.1 codename Straight Razor) >> Maximum connections set to 1024 >> Listening on 0.0.0.0:9292, CTRL+C to stop ... HTTP_AUTHORIZATION => Basic Y2FzaWFubzp0dXR1 REMOTE_USER => casiano ...
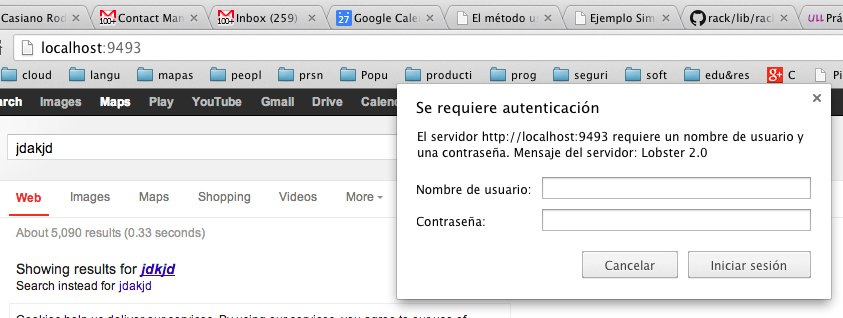
Autentificación Básica: vista en el navegador
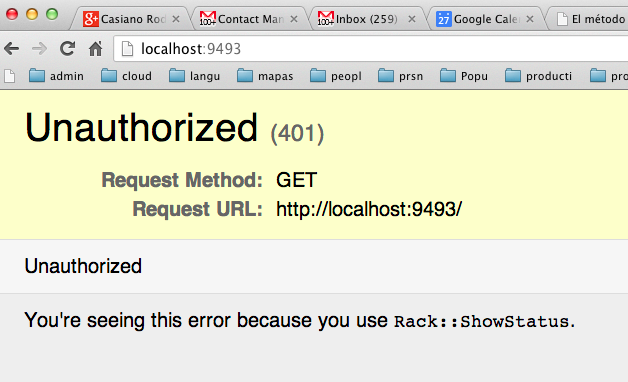
Si pulsamos "cancel" obtenemos: